By Nishant Tiwari
In the age of abundant online financial news, stock investors face the challenge of monitoring vast amounts of information related to their stock interests when making investment decisions. AlgoFabric provides a centralized platform where you can access all financial news and sentiment trends for your preferred stocks. AlgoFabric leverages Natural Language Processing (NLP) capabilities to curate information that assists in making well-informed decisions for the stock of your choice.
For the security and integrity of Algofabric, we conducted a comprehensive AWS security assessment using ‘AWS Security Hub’ and ‘AWS Config’. This evaluation encompassed a detailed examination of our AWS infrastructure, configuration, and access controls. Our objective was to ensure that our AWS environment adheres to industry best practices and maintains the highest standards of security which resulted in a considerable improvement in our score:
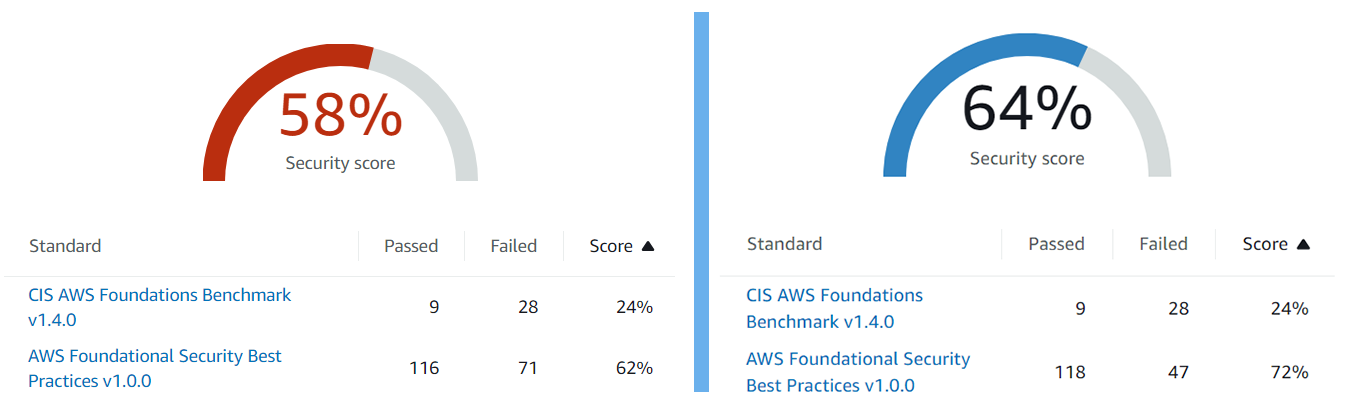
In this guide, we’ll share the actionable steps we explored to enhance the security of our AWS environment based on findings from AWS Security Hub and industry best practices. On AWS security hub dashboard one can find the security flaws classified into four categories based on their severity:
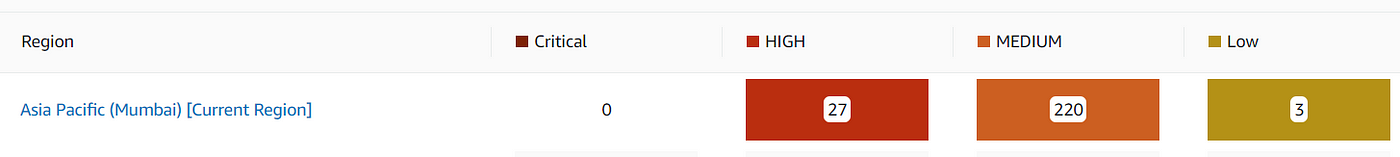
Based on the findings we have divided the security findings into following 4 categories:
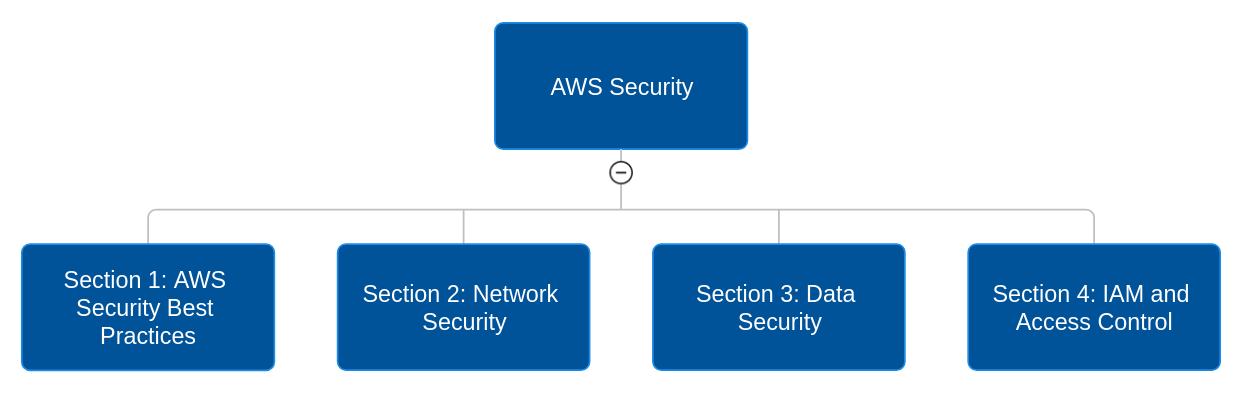
Section 1: AWS Security Best Practices
Enabling Multi-Factor Authentication (MFA)
Finding: Hardware MFA should be enabled for the root user
Severity: CRITICAL
One of the foundational steps in securing your AWS account is enabling Multi-Factor Authentication (MFA), especially for the root user. Hardware MFA adds an extra layer of security, making it significantly more challenging for unauthorized users to access your AWS resources.
In addition to this configure IAM password policies to enforce strong password requirements.
Avoiding Wildcard Actions
Finding: IAM customer managed policies that you create should not allow wildcard actions for services.
Severity: LOW
This finding raises a security concern about IAM policies in AWS. Some policies use wildcard actions (*), granting unrestricted access to entire services, posing security risks like unauthorized access and data breaches. Restricting policies to the least privilege level is crucial for enhancing security.
Solution:
Firstly, audit and identify IAM policies that contain wildcards, and secondly, refine these policies to grant only the minimum required permissions. Implement a strict “principle of least privilege” approach, where users and roles should have access only to actions they genuinely need.
Avoiding IAM Policy Attachments
Finding: IAM users should not have IAM policies attached
Severity: LOW
If the number of users are very high in that case instead of applying polices to users, it should be applied to groups and roles. Assigning privileges at the role or group level reduces the complexity of access management if number of users is very high.
Solution:
- Review and detach unnecessary IAM policies from users.
- Implement the principle of least privilege for IAM permissions.
Section 2: Network Security
Restricting High-Risk Ports
Findings: Security groups allow unrestricted access to ports with high risk.
Severity: CRITICAL
Solution:
- Review and modify security group rules to limit access to specific IP ranges or required ports.
- Implement network access control lists (ACLs) for further traffic restriction.
Unused Security Groups:
Unused security groups clutter security configuration, potentially leaving open security holes, and can lead to confusion when managing your infrastructure.
Therefore all unused security groups should be identified and removed.
Section 3: Data Security
For AlgoFabric we make use of S3 buckets to store plethora of data including the prediction models. So we prioritize the S3 bucket’s security. Here are some of the crucial findings regarding the same:
Enabling Lifecycle Policies
Findings: S3 buckets with versioning enabled should have lifecycle policies configured.
Severity: MEDIUM
Absence of lifecycle policies for S3 buckets with versioning means that organizations may miss out on optimizing their storage costs or efficiently managing object retention.
Solution:
- Implement lifecycle policies to manage object retention and deletion effectively.
- Optimize storage costs.
Securing S3 Buckets
Prohibiting Public Write Access
Findings: S3 bucket should prohibit public write access.
Severity: CRITICAL
Certain S3 buckets allow public write access, where users are allowed to upload files or data to a publicly accessible S3 bucket, such as in a file-sharing or data collection scenario. Apart from such cases Public write access should be prohibited.
Solution:
- Update S3 bucket policies or Access Control Lists (ACLs) to deny public write access.
- Restrict permissions to authorized users or applications.
Prohibiting Public Read Access
Finding: S3 buckets should prohibit public read access.
Severity: CRITICAL
Make sure public read access is given to only the necessary resources like Public Websites, Public Data Repositories, Content Delivery, Shared Resources.
Solution:
- Modify bucket policies or ACLs to revoke public read permissions.
- Ensure that only authorized users or resources have access to the bucket.
EBS Volume Encryption
Findings: Attached EBS volumes should be encrypted at rest.
Severity: MEDIUM
Amazon EBS encryption is a simple way to secure your EBS resources linked to your EC2 instances. This approach eliminates the need for you to establish and protect your own key management system. Instead, Amazon EBS encryption leverages AWS KMS keys during the process of crafting encrypted volumes and snapshots.
Solution:
- Enable encryption for EBS volumes to protect data at rest.
- Comply with data privacy regulations.
Use non-default database engine ports for RDS instances
Finding: RDS instances should not use a database engine default port.
Severity: LOW
The default ports for database engines are well-known, making them vulnerable to potential attacks. Changing these ports enhances security by adding an extra layer of obscurity, making it more challenging for attackers to identify and target RDS instances. By choosing unique port numbers, organizations reduce the risk of unauthorized access, protecting their databases from common threats.
Block Public Access settings
Finding: Block public access settings are disabled for the S3 bucket.
Severity: HIGH
When the “Block public access” settings are disabled for an S3 (Simple Storage Service) bucket, it means that the bucket is not configured to prevent public access to its contents indicating that anyone with the necessary permissions, including anonymous or public users, can potentially access and interact with the data stored in that bucket.
Solution: Enable “Block public access” settings for the S3 bucket. Review and adjust the bucket policies and access control lists (ACLs) to ensure that only authorized users and applications have access. Additionally, use IAM (Identity and Access Management) policies to control permissions and restrict public access.
Section 4: IAM and Access Control
IAM User Cleanup
Findings: Unused IAM user credentials should be removed.
Severity: LOW
The presence of unused IAM (Identity and Access Management) user credentials in AWS accounts poses a significant security risk. Dormant credentials can be exploited by unauthorized entities, making it essential to regularly audit and clean up IAM users to maintain a secure AWS environment and reduce the risk of breaches and unauthorized activity.
Solution:
Conduct periodic IAM user credential reviews. Start by identifying unused or unnecessary IAM users, removing their access, or disabling accounts when no longer needed. Use AWS Identity and Access Management best practices to apply the principle of least privilege, ensuring that users have only the permissions required for their roles.
Encrypt SNS-topics with KMS(Key Management System):
Findings: SNS topics should be encrypted at-rest using AWS KMS.
This encryption safeguards sensitive information, such as messages, notifications, or subscribers’ details, making it significantly more challenging for unauthorized parties to gain access to the content. This security measure is essential for compliance with data protection regulations and to maintain the confidentiality and integrity of data transmitted through SNS topics.
Solution: KMS doc for AWS explains wide variety of KMS available for the customers and their specifications that one can choose as per the security they want.
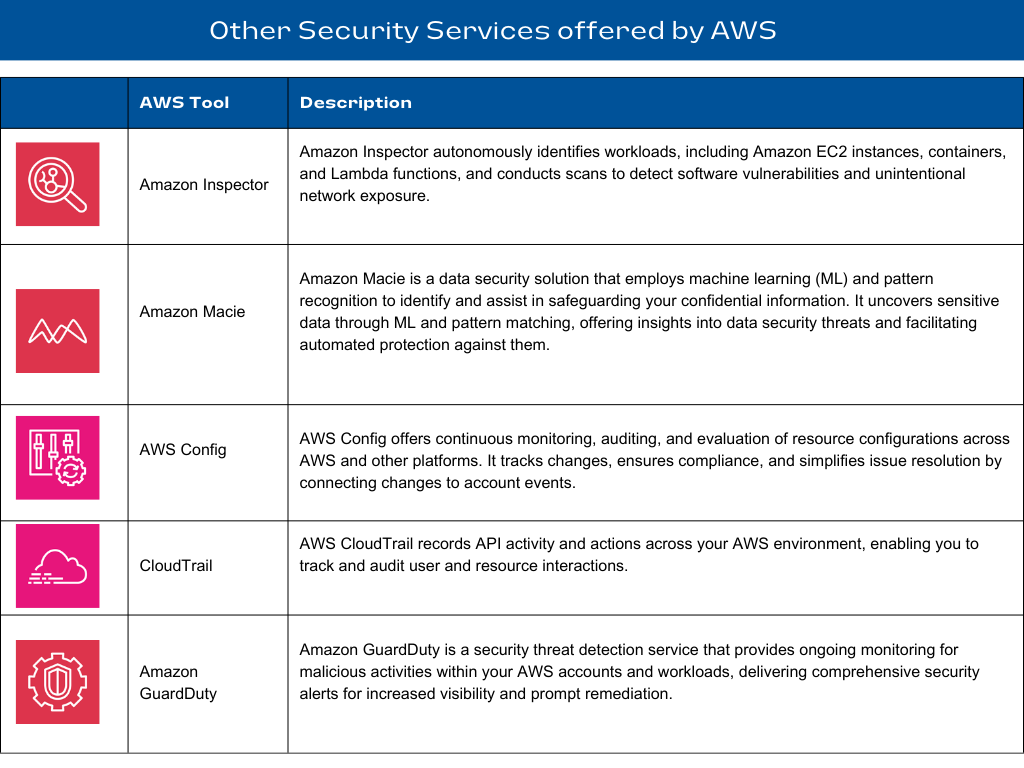
Some of the crucial Security Services offered by AWS: